Thanks to modern technologies, it’s easier than ever for businesses to deliver meetings, webinars, and events via the internet. While the move toward virtual and hybrid events meetings was accelerated due to COVID-19 lockdowns and safety concerns, businesses have embraced the opportunity to reach larger and more distant audiences online.
But businesses need to balance these benefits with new risks and threats. This is especially true today, when virtual and hybrid events are reaching maturity and the initial novelty around the format has given way to clearer measures for performance. As organisations are responsible for safeguarding a huge amount of attendee and speaker data, cybersecurity is a crucial concern for online event managers. Depending on their objectives, hackers may attempt to steal your business data, attendee personal and payment data, or they may seek to spread malware to attendee devices.
Robust cybersecurity is key to minimising these risks and protecting your reputation, along with your audience’s data. For organisations, another concern is complying with strict data privacy regulations like GDPR in the EU or American state-specific laws like the CCPA in California. Failure to meet GDPR compliance, for instance, can cost €20 million or up to 4% of annual global turnover.
While Interprefy isn’t a data security company, we are ISO 27001 certified and our Information Security Management Systems is aligned with standards in the area of data security and recommended best practices. Drawing from our expertise and experience with online and hybrid events, we’ve put together a checklist for organisations looking to improve their event cybersecurity. Let’s dive in.
Your online event data security checklist
Click here to open and download the checklist
-
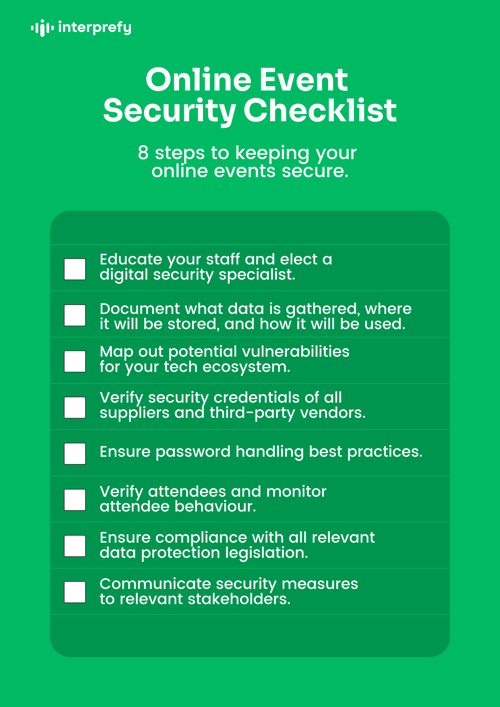
Educate your staff and elect a digital security specialist
Every device, software program or user account is a potential entry point into your virtual event. Training staff in cybersecurity is essential to minimise the risk of being hacked. At the same time, you should elect a digital security champion to educate your staff, keep up with the latest cybersecurity measures and push for greater data protection.
Your digital security specialist can be CISO-level or lower, as long as you establish clear accountability and your security officer is given the resources to improve data security. When promoting someone into the role of digital security specialist, dedicate resources to helping them become cybersecurity experts. -
Document exactly what data is gathered, where it will be stored, and how it will be used
To protect your data, your organisation needs a clear idea of exactly what data has been collected and where this data can be found. Developing a data and asset inventory system is key to gaining sightlines over your data collection and storage. Once you have these sightlines, ensure that only essential data is collected and that the purpose of this data is understood from the outset. This will help you streamline your data collection and prevent you from filling your servers with sensitive information that has little value to your organisation.
With a data inventory, you can also schedule data disposal to prevent data from being forgotten about and potentially stolen at a later date.
After the data inventory has been established, remember to put in place a data classification schema according to the principles of data availability, integrity and confidentiality. -
Map out potential vulnerabilities for your tech ecosystem
Would you put a coin in your pocket if you knew your pocket had a hole in it? Probably not. Similarly, you wouldn’t store your data in a vulnerable system — where hackers can easily get at your data.
So how do you patch the holes in your system? The first step is to map out all the technologies and tools that are used in your event. Each is a potential vulnerability that can be exploited if the provider’s security measures are outdated or other precautions have not been taken. Armed with a systems map, your data security specialist can work to limit vulnerabilities at each point that data moves from one system to another. -
Verify security credentials of all suppliers and third-party vendors
When using event technology services, aim to partner with vendors who have data security accreditation compliant with reputable institutions such as the International Organization for Standardization (ISO). These certifications prove that vendors follow strict and globally recognised cybersecurity standards.
At Interprefy, for instance, our company has achieved ISO 27001 accreditation. For our partners, our accreditation shows how committed we are to protecting their data and keeping events secure. -
Ensure password handling best practices
Did you know that the word “password” is still one of the most popular passwords used within Fortune 500 companies? As NordPass research shows, poor password handling is a top reason Fortune 500 companies have been affected by more than 15 million data breaches.
One of the easiest strategies to improve event security is to adopt password best practices. This includes using a reputable password manager to securely generate and keep track of complex passwords. Another strategy is to use two-factor authentication (2FA) for your online accounts. 2FA boosts account security by requiring that users identify themselves by more than a username and password.
Like other security-conscious event tools, Interprefy offers 2FA. We also offer active directory integrations — this measure ensures that only users with the right credentials can access the platform, such as being registered as an event participant. -
Verify attendees and monitor attendee behaviour
To reduce the risk of bots, spam or trolls disrupting your event, use tools to verify attendees during the registration process. Tools such as CAPTCHA, QR codes, email verification and multi-factor authentication help you screen and verify the identity of each attendee.
Once the event has started, have one of your staff monitor attendee behaviour. Look for attendee complaints, foul language and disruptive behaviour. If attendees are hampering the event experience, remove them from the event. -
Ensure compliance with all relevant data protection legislation
While legislation like GDPR in Europe and CCPA in California are leading the trend, governments around the world are implementing regulations to protect user data. Achieving compliance with these regulations is critical to avoiding costly fines. On the positive side, simply being compliant brings with it many security and privacy benefits, as there are fewer vulnerabilities across the data management ecosystem.
Under global data regulations, organisations are defined as data controllers and the digital platforms you work with are defined as data processors. For your event to meet global regulations, both your organisation and your event management provider must be compliant. -
Communicate security measures to relevant stakeholders
Informing attendees of security measures will increase their confidence and comfort. That said, don’t provide too much information, as this can be used by cybercriminals to prepare a more sophisticated targeted attack.
To help your attendees protect their data, consider sending them a list of cybersecurity best practices. This can include advice on updating their devices before joining the event and to only share their information with attendees that they trust.
What to do if a data breach occurs
No matter how slim, there is always a chance of a data leak. While being diligent about cybersecurity is pivotal to preventing leaks, having a plan to deal with data breaches is another important step in limiting your liability. In the event of a data leak, you should consider the following steps:- Identify the leak — the first step is to figure out what data has been compromised, how sensitive the data is and how many people were affected.
- Decide who to notify — consider how serious the breach is. After reporting the breach internally, decide which parties need to be notified. You may want to notify vendors, your customers or even the police.
- Share a report with the relevant data protection authorities — report your situation to the relevant authorities and provide as much detail as possible. They will use this information to figure out what happens next. The information you share is valuable in shaping regulation and identifying data security trends.
- Learn from the leak — how did the leak happen and what could you have done differently? The lessons you take from a data breach will be valuable in improving security and preventing leaks from occurring in the future.
Why partner with Interprefy
At Interprefy, we offer a remote simultaneous language interpretation platform that enables multilingual meetings and events across the globe.
As an ISO 27001 certified interpretation partner, we’re constantly updating our platform to ensure that we’re following the latest security measures. Our platform features best-in-class security standards and protocols for encryption and transmission, such as TLS 1.2 — the most secure encryption protocol available today. Interprefy also makes use of AES-256-GCM encryption, two-factor authentication and WebRTC for secure, real-time audio and video streaming.
We understand the importance of keeping your events secure, which is why we offer ongoing support to address issues as and when they arise. So if you’re looking for a security-minded interpretation provider for your online events, then we can help.
Click the button below to contact a member of the Interprefy team. We can discuss your online event interpretation needs, along with how our platform can meet your data security requirements. 
Want to learn more about trends dominating the events industry?
Online event data security is one of the key trends shaping event management. To learn about the other major industry changes, then check out our 2022 guide to event management trends. In it, we discuss how event planners can prepare for the future while innovating their events. Follow the link for your free download.


-min.png?width=1040&height=800&name=Blog%20Header%20(29)-min.png)

 More download links
More download links



